Security is an extremely important aspect of software development, server management, and application development these days.
And if you use Linux, you're in luck – it comes with an excellent feature called SE Linux that helps you add an additional layer of security.
What is SE Linux?
SE Linux was developed by the NSA (National Security Agency) to serve government-related security tasks.
SE Linux stands for Security Enhanced Linux. It gives system administrators more control for providing access to files and processes. With SE Linux, admins can define a context and tag files and permit them within that context.
Access and permissions are usually inherited based on user groups. But there are some sources (like web servers and processes) that need access to network ports and kernel processes. These are usually spawned by the root user or users with special access. SE Linux helps you limit who can access these special processes.
How to work with SE Linux
SE Linux comes by default in most Linux distros. In this post, I will be working on Fedora.
Just keep in mind that working with SE Linux requires sudo or root access.
The SE Linux configuration file is located in the /etc/sysconfig/selinux folder. Let's view its contents:
SE Linux Modes
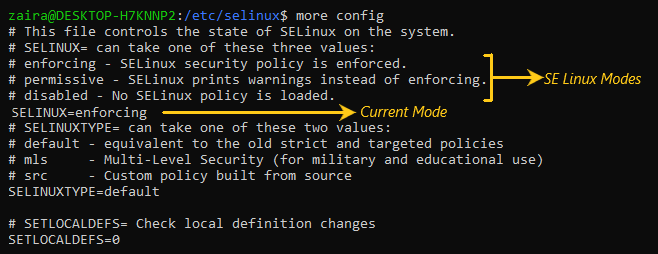
In the config file, we can change the modes and choose any one from the below:
-
Enforced: Enabled by default, filters based on defined policies.
-
Permissive: Doesn't enforce the defined policies, but records all of the attempts in log files. This mode is useful for troubleshooting.
-
Disabled: SE Linux is completely disabled. This is not recommended as it might expose your system to threats. Also, reverting back to enforced could create certain discrepancies.
You can check your current SE Linux mode with the below commands:
-
getenforce.
-
sestatus.
If you only need to change the mode for the current session, you can use the below commands:
-
sudo setenforce 0 - sets permissive mode for current session.
-
sudo setenforce 1 - sets enforcing mode for current session.
SE Linux Policies
In SE Linux, policies define access to users. Users define access to roles and roles define access to domains. Domains then provide access to certain files.
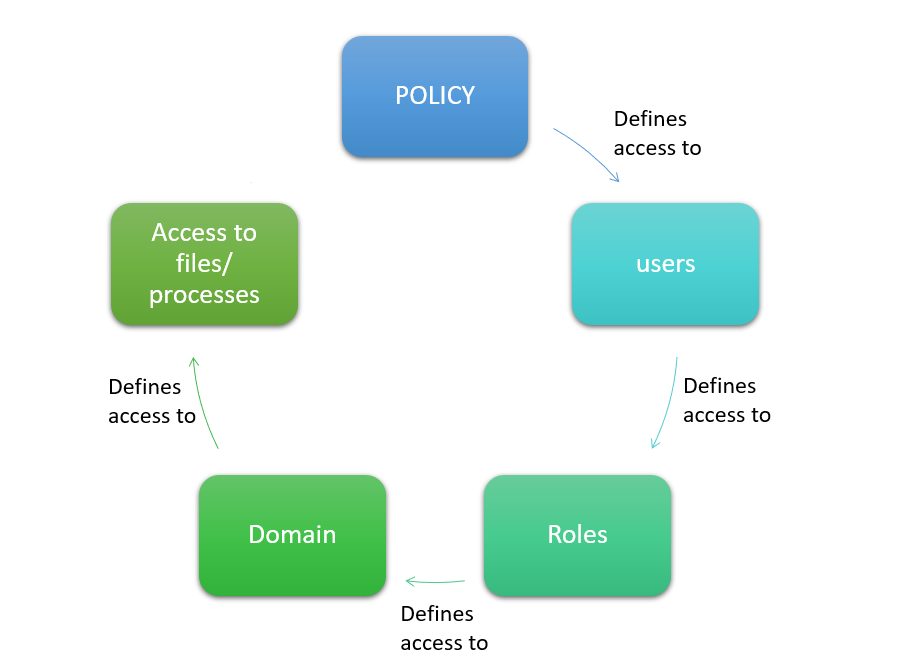
To change and modify accesses, 'booleans' are defined. We'll look into booleans in the next section.
How to manage SE Linux policies with booleans
As you now know, SE Linux policies are managed by booleans.
Let's see a working example of how you'd view and set a boolean. In this example, we will set booleans specific to httpd.
First, list all modules specific to http – getsebool -a | grep httpd.
Here -a lists all booleans.
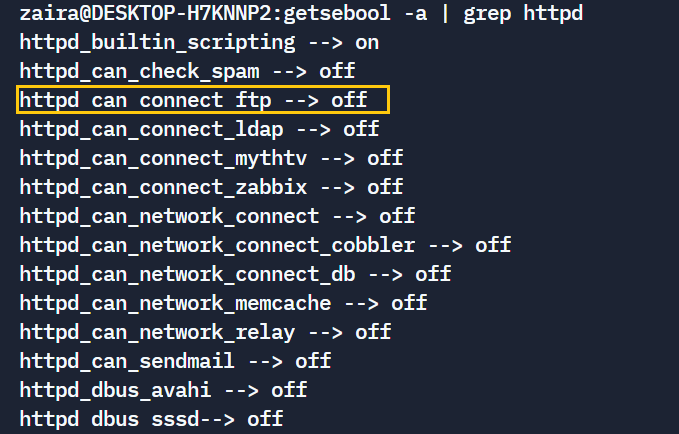
Next, let's select and change the yellow highlighted boolean in the code above:
getsebool httpd_can_connect_ftpNow, set the value to allow.
setsebool -P httpd_can_connect_ftp 1In the command above,
-
The flag P is used to make the change permanent even after reboot.
-
1 is enabling the boolean.
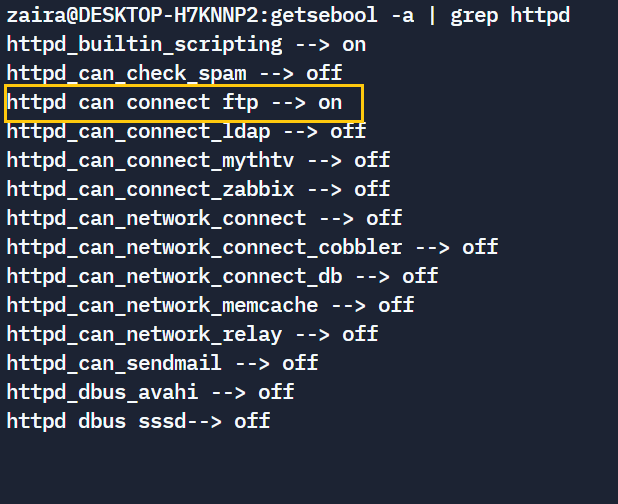
Now, when you list the process again, its value will be allowed.
SE Linux Architecture
The diagram below explains how SE Linux validates an attempt from source:
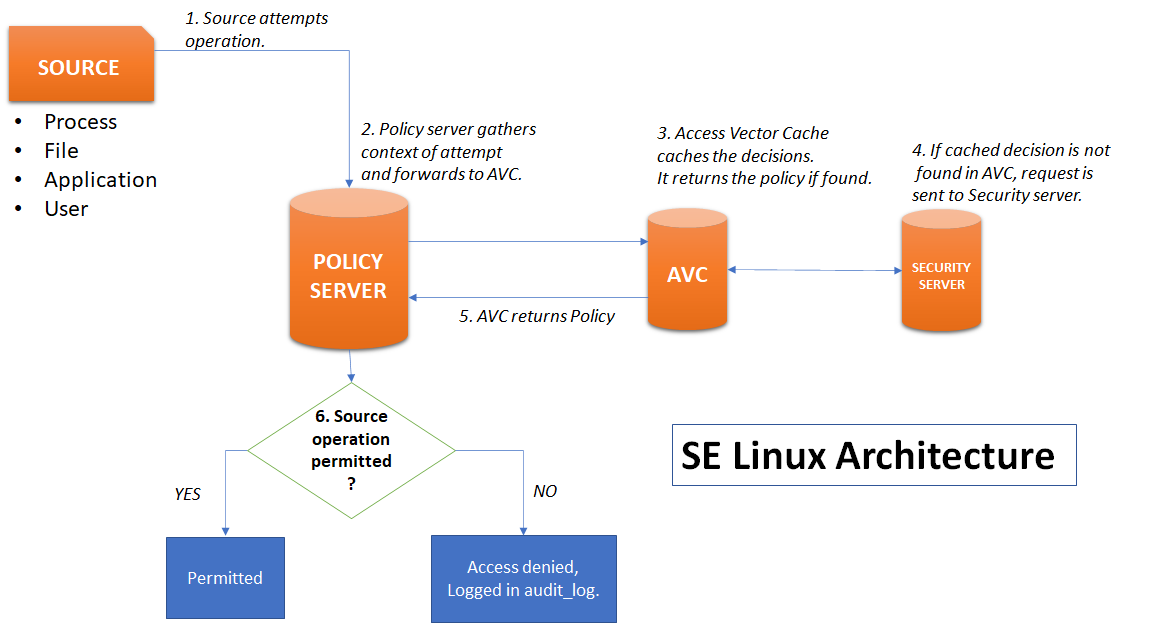
Troubleshooting and SE Linux Logs
SE Linux produces very detailed logs for each attempt. You can find the logs and view them here: /var/log/audit.
While troubleshooting, you should move into 'permissive' mode so all events can be recorded in the logs. Although policies are not being enforced, attempts are being recorded in logs.
How to disable and enable SE Linux
Disabling SE Linux completely is never a good option. But there are certain scenarios where policies can be by-passed such as when troubleshooting.
Instead of disabling SE Linux if you run into a small issued, it is better to invest some time in troubleshooting.
But if you really need to disable SE Linux, follow these steps:
-
Change the mode from 'enforcing' to 'permissive'.
-
Change mode from 'permissive' to 'disabled'.
Author: Zaira Hira
https://www.freecodecamp.org/news/securing-linux-servers-with-se-linux/





