Today in companies we are used to networking. In the office it is common to share resources such as a printer, have a server where information is stored or shared and more. However, sometimes you work with confidential information and secret projects, to which not everyone should have access. Either because we want that information not to have all workers, ends up leaking through the Internet in an attack, or both. So what you want is to create an isolated network to keep this valuable information safe. In this tutorial we are going to know if an isolated network is really safe and to learn a lot about it.
The first thing we are going to learn is what an isolated network is and what characteristics it must have, so that it is as secure as possible in a company. Then we will discuss several methods with which, if you are not careful, could violate the security of this type of network. We will also discuss some examples to partially imitate these concepts in our home networks.
What is an isolated network and requirements to be secure
An isolated network could be defined as one that distributes packages to and from local systems. Also, although it has routes to some other network defined, it does not carry messages to other networks. In this sense, your computers will not be able to communicate or network with other computers except those that make up your own network. Thus, they would be isolated from other company networks in order to keep the information stored there more protected.
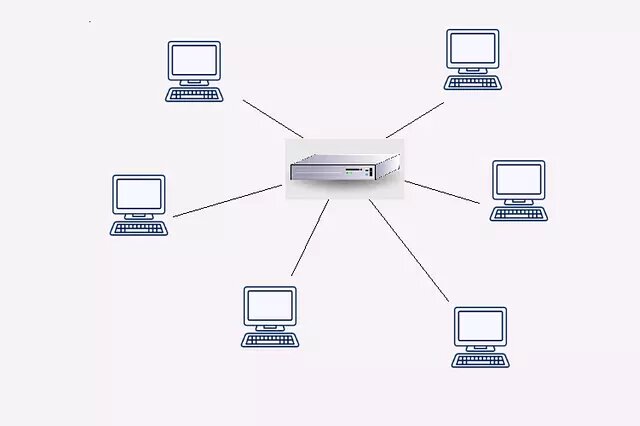
The best example of an isolated network that we could have in a company would be one that is totally separate from the main network. This means two things, one that we would not have access to it from the Internet because it would not have a connection of this type. The other would be that the other networks or subnets of the company would not be able to reach it since they would not be connected to it via Ethernet network cable, Wi-Fi or other means.
Regarding the requirements that this isolated network should have to remain secure, our company should have a series of rules:
-
Computers on the network should have virus protection and be updated manually at least once a week.
-
We must have a device control system for each machine, which prevents the connection of USB sticks or other storage devices, except those that are in a list of trusted devices.
-
Prohibition of the use of smartphones and other devices with an Internet connection in the place where our isolated network is located.
A priori, it could seem an almost perfect situation, very difficult to violate, but sometimes, mistakes are made that end up damaging your security.
The danger of smartphones and other media that offer Internet connections
On many occasions, security experts believe that an isolated network does not need special protection to protect its information. The reason they put forward is that threats cannot penetrate the network. However, they are wrong because isolation is not sufficient guarantee to stay safe.
One of these typical failures is caused by human error and overconfidence. Employees in charge of updating antivirus or other programs find that this weekly task of updating them is boring and heavy. Then they are tempted to use a smartphone, a USB modem or other means to be able to use a computer with an Internet connection and perform an automatic update.
Simply doing so does not imply network attacks, Internet malware, or other security problems. The problem usually comes because those in charge of updating the antivirus do not do it weekly. Cybercriminals can then infect that computer with Trojans, spyware, and eventually end up gaining access to the entire isolated network. Thus, from that moment they will be able to collect all the information they want until an antivirus update cuts them off or they are detected.
USB sticks and trusted devices are a risk
An isolated network to perform its updates and maintenance has a series of exceptions that allow it to connect to them. In this case it would be the trusted media and devices. A typical case can be the use of a USB memory. The problem would come when that removable memory is used in more places. In that sense, we are not 100% guaranteed that such a drive will not be used to copy files to and from the system, or on a non-isolated network segment. So that this does not happen, you would have to be very strict with the safety rules and be very aware.

Apart from those removable media such as USB memories or external hard drives we have more risks. Sometimes members of the security team connect their laptops to an isolated network because they have to configure some equipment on the isolated network. In these cases, the use of these trusted means can become a source of malware infection. The problem is that this infection will run freely for at least a week, which is when we would have the next update scheduled.
The threat we face will depend on the type of malware that has infected our isolated network. So because of this we could face:
-
The attempt to seek confidential information and when we connect to update it is sent abroad.
-
Equipment software is altered and may end in a case of corporate sabotage.
-
Ransomware infection of the entire isolated network, encrypting all data and rendering the network unusable
Therefore, depending on the security problem, we will have the isolated network completely compromised. Sometimes an employee who is disgruntled, blackmailed, or tempted by a large sum of money can endanger that isolated network. Thus, an employee with access to it could connect to it a mobile device or of another type that can facilitate access to the outside. For this reason, the people in charge of the maintenance and care of this isolated network must be carefully selected. In that sense, you have to be a trained, rigorous and reputable professional.
So you can have an isolated network in home environments
Sometimes you may also want to create an isolated local network in your home environment. Nowadays, remote work from home is increasingly on the rise. However, not all family members are very strict about safety. In this sense, some type of malware could spread that affects the local network. For this reason, using a second router that we have at home, we could create two networks:
-
The 192.168.1.X range for working devices.
-
The 192.168.2.X range for entertainment devices and for the rest of the family.
Also some manufacturers such as ASUS and the AVM FRITZ! Box offer a technology to isolate the WiFi clients, so that they cannot communicate with each other with other wireless clients. The same could be done using wired networks. Let's take an example with a FRITZ! Box so that the wireless clients do not see each other:
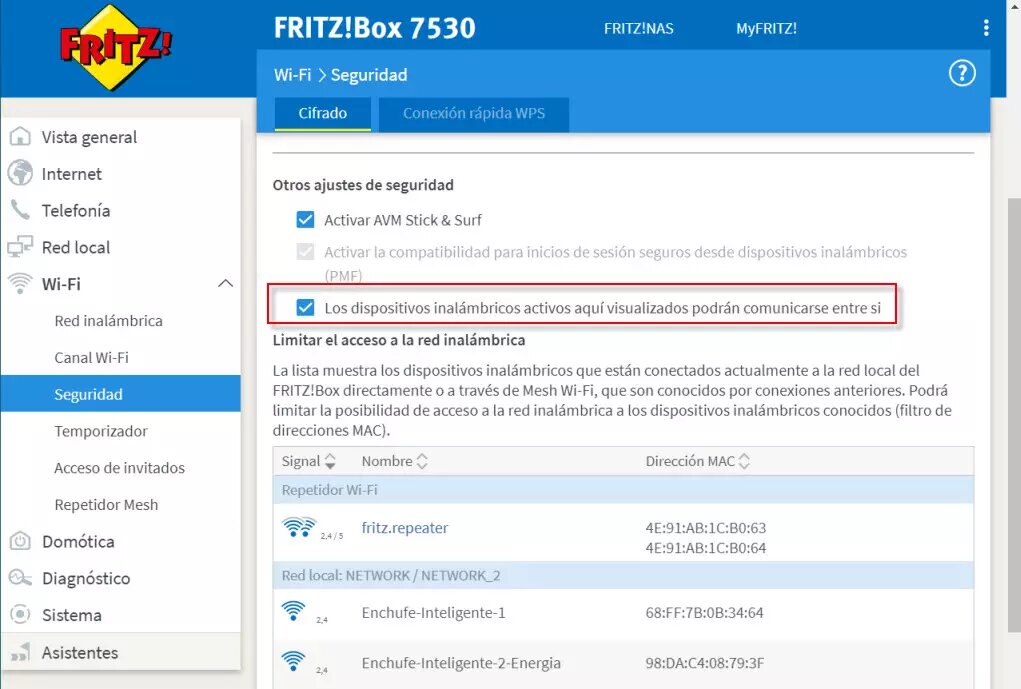
In this case, if we deactivate the box in the red box, the devices will not be able to communicate with each other. However, we could also create a guest network from scratch that is totally isolated from the main network, in this way, we can configure a wired and wireless guest network, where they cannot communicate with the main wired or wireless network. In addition, it would also be advisable to segment the local network into different VLANs, but to do this you will need a router compatible with VLANs and also a manageable switch to create them correctly.
As you have seen, having an isolated network is not totally safe, since human intervention or a bad configuration could make it vulnerable and attack it. In addition, in home environments we could also configure an isolated network of guests, so that they do not communicate with the main network.





