The Internet giant Cloudflare often operates in the shadows, or rather, not directly with the Internet user. Being an Internet infrastructure company, it operates for other companies managing connections to servers and web pages. However, their work is more important than it seems, for example, it manages to mitigate what has been reported as the largest DDoS attack in history.
The attack took place last month and the target was one of Cloudflare's clients that operates in the financial industry and has not been disclosed. Like any other DDoS attack, the attacker used a large number of devices to make HTTP requests to the victim's network in order to crowd the server and bring it down.
It wasn't a bandwidth DDoS attack but a volumetric one. These differ in that they seek to send all possible HTTP requests to consume the server's CPU and RAM, thus ensuring that the server does not operate directly. Bandwidth DDoS attacks seek to obstruct the bandwidth of the Internet connection to slow down or sometimes block the connection.
20,000 devices infected with a version of Mirai
The attack reported by Cloudflare was of around 20,000 infected devices throwing up HTTP requests. In total, they achieved a maximum of 17.2 million HTTP requests/second. It's a spectacularly high figure, three times higher than the previous record reported.
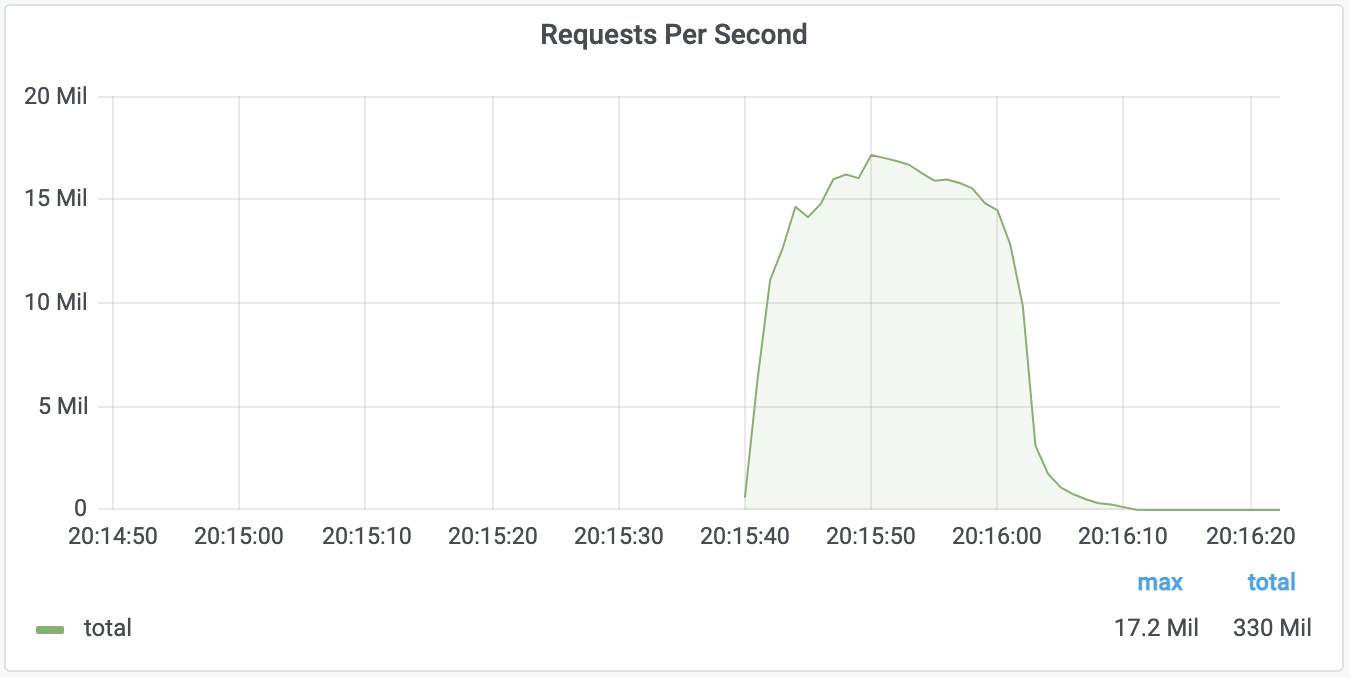
To put this attack in context, Cloudflare says that in its last quarter it averaged a total of 25 million legitimate HTTP requests / second worldwide. The 17.2 million from the attack was 68% "extra work" on what Cloudflare typically operates.
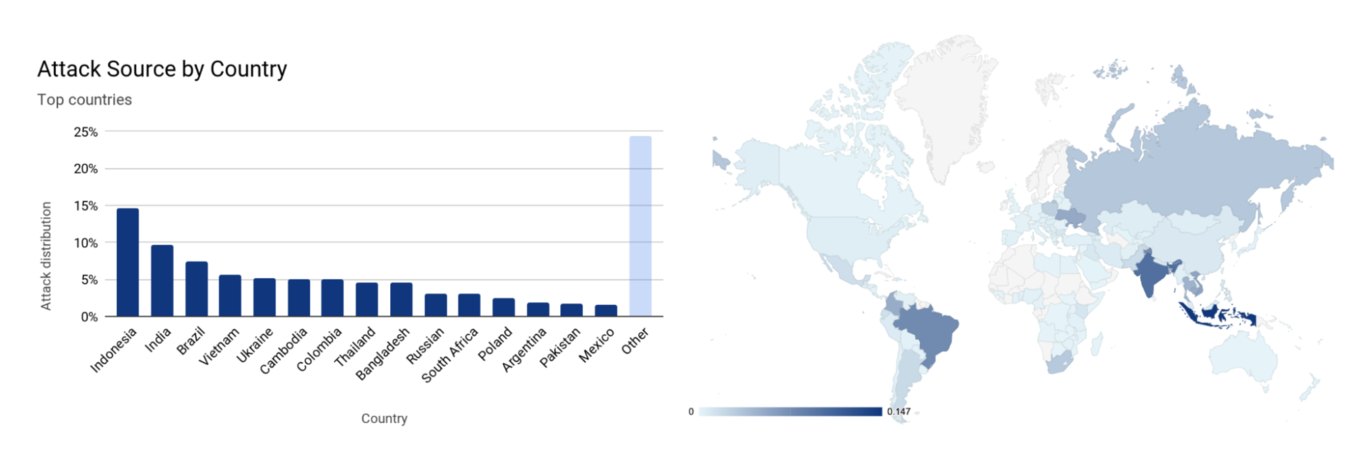
Where did they come from? According to the IPs of the devices that sent the requests, almost 15% were from Indonesia, almost 10% from India and just over 7% from Brazil in the TOP 3 countries. Cloudflare believes that these are devices infected by the Mirai malware or a modified version of it.
Mirai is malware first discovered in 2016. It spreads by infecting Linux-based devices that are generally IoT. For example, it infects security cameras, routers, or even smart bulbs. It has the peculiarity of spreading only thanks to the use of default credentials.
A year ago Amazon AWS revealed another fast-paced bandwidth DDoS attack this time around. The attack they claimed to have mitigated achieved a traffic spike of 2.3 Tbps. An outrage that, once again, was stopped before it reached Internet users.





