The VPN market is still dominated by the IPSec/L2TP standard, which has been around since the 1990s. Since then, the technology has become ubiquitous, but some VPN providers have been looking into the next generation of VPN technology, which promises to be faster and more secure. One such company, WireGuard, claims to have created the future of VPNs.
What is it? The WireGuard protocol is one of the latest to create a stir in the VPN market. The open-source technology was created by Jason A. Donenfeld, who has since become the CTO of a company called Edge VPN.
In a nutshell, WireGuard is a new VPN protocol. It is not a software, but a set of instructions that allows you to create VPNs very easily. It has been developed as an alternative to IPsec, OpenVPN and similar VPNs, but faster and easier to use. In essence, WireGuard is based on ideas from the IPsec protocol.
WireGuard is an extremely simple, yet fast and modern VPN that uses state-of-the-art cryptography. It aims to be faster, simpler, and more versatile than IPSec, while avoiding the huge headache (especially on NATed networks). It aims to be considerably more efficient than OpenVPN. WireGuard is designed as a general-purpose VPN to run on embedded interfaces, suitable for many different circumstances. It runs on top of the UDP protocol, so it is considered a layer 3 tunnel.
How does Wireguard VPN work?
WireGuard is a P2P protocol, this means that instead of requiring a server, WireGuard has the ability to open a tunnel between two devices, only certain configurations need to be applied for establishment.
The way connections are established is very similar to an SSH tunnel, users need to generate public keys with WireGuard and exchange them, this is WireGuard's way of identifying VPN peers , encrypting data and at the same time verifying that it is the correct recipient.
In addition to the type of cryptographic configuration, it is necessary to configure the networks, by this we mean that IP ranges and addresses need to be configured, this is necessary because WireGuard verifies that the packets come from allowed networks, if they do not, it would discard the packet, that is another point of its security.
As far as cryptography is concerned, WireGuard implements modern applications such as Curve 25519, ChaCha20, Poly1305 plus BLAKE2 and SipHash2-4. This makes it very secure and flexible.
Wireguard generates a new interface (like eth0, wlan1).
When a device has to send data from A to B, the first thing it verifies is that the device it wants to communicate with belongs to the WireGuard network. If it does not belong, it discards the packet. If it does belong, it performs the following procedure:
1) The packet is encrypted with a source public key.
2) The packet is sent by an IP address, host and port.
3) When the destination receives the packet (encrypted with the server's public key) it only has to decrypt it with its private key.
4) Finally, verify that the person who sent it is an authorized device, otherwise, discard the package.
In this way, we could analyze that when we send WireGuard packets, the IP addresses work as a routing table, and when we receive them, it works as an access list of allowed addresses.
Wireguard vs IPSEC vs OpenVPN
In addition to the main differences in security and keys compared to IPSEC or OpenVPN, WireGuard has differences in relation to speed, latency and roaming.
As far as Roaming is concerned, WireGuard relies on the device's network configured on the server side, in any current VPN, the moment the network is disconnected, we must establish the tunnel again, for example, if we are connected to an IPSEC tunnel via Wifi and the connection changes to LTE or 4G, we must establish the tunnel again, with WireGuard we can maintain the connection even if the WAN IP address changes.
Speed and latency in WireGuard VPN.
WireGuard has improvements in speed and latency compared to OpenVPN and IPSEC. Since it uses faster cryptography and runs inside the Linux kernel, WireGuard can transfer data faster than other protocols and even lower their latency.
Both OpenVPN and WireGuard are open source, have very few vulnerabilities, and will require additional configuration files to set up on most devices. The difference is that WireGuard uses much more advanced cryptographic libraries and is much more efficient.
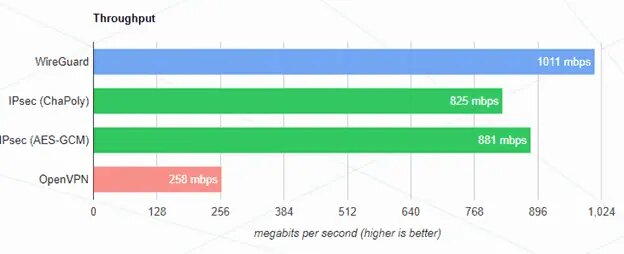
WireGuard Vs OpenVPN vs IPSEC in relation to their speed.
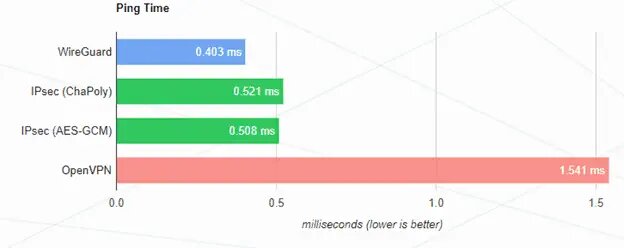
WireGuard latency comparison.
This is a big plus because we could run services through a Wireguard tunnel with low latency requirements, such as VOIP, streaming, and even gaming.
Configuring WireGuard with Mikrotik
Mikrotik has support for WireGuard VPNs starting from version 7.1beta2, therefore, since it is working in beta versions, it is not recommended for use in production environments. Currently, at the date of publication of this article, the current beta version is: 7.1beta6.
In this configuration we make the connection between two Mikrotik Routerboards, but the connection could be established with an end client such as a computer or mobile phone, through different applications that we will share in the last links of this article.
Configuring WireGuard Server with Mikrotik
Let's start by setting up one of the P2P endpoints, we'll call this side of the tunnel the "server". Remember that you need at least version 7.1beta2 for this setup to work.
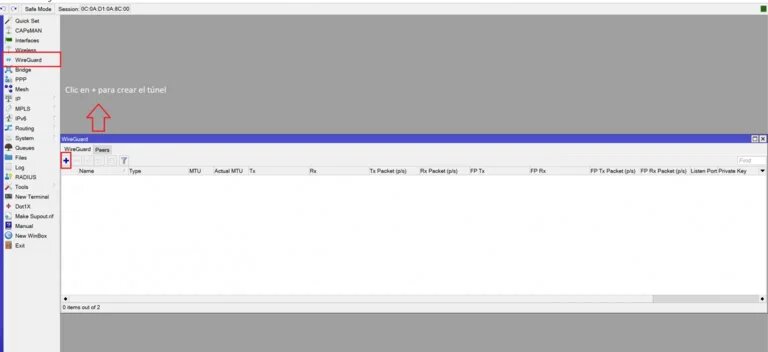
Click + to create the tunnel.
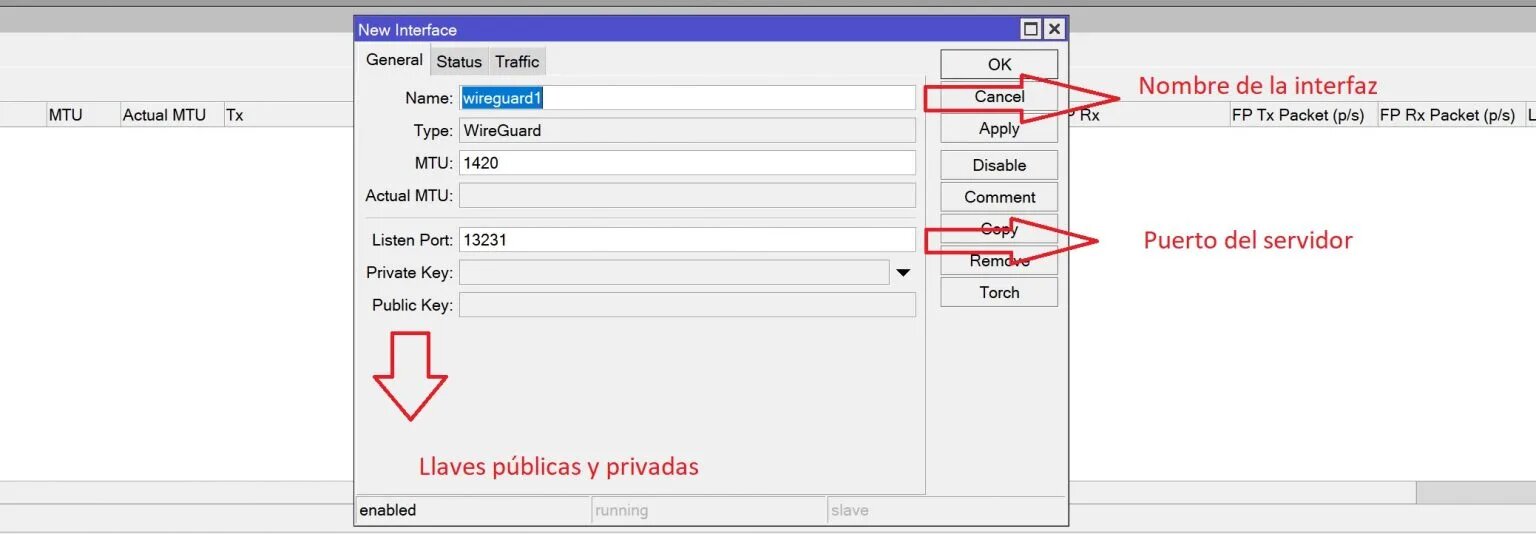
We just need to click on “Apply” to generate the server’s public and private keys.
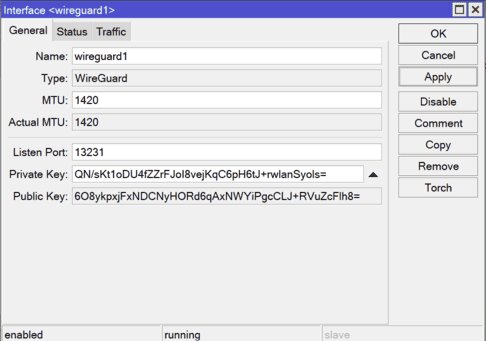
Public and private keys created.
Configuring Server Networks
We have assigned two IP addresses for different interfaces, we will take that the Ether2 interface will be our WAN interface and then the Wireguard1 interface is the interface that was configured when creating the tunnel, we will assign IP addresses to each of the interfaces in this lab. In a real environment, the WAN interface might take an IP address from a DHCP client.
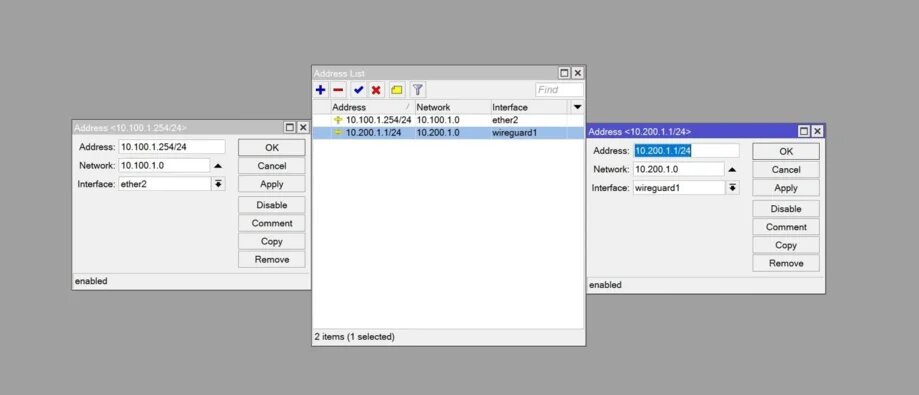
Creating the WireGuard Client
We will perform the same steps that we did previously when we created the server. Go to the WireGuard option and click on + to create the server, we will leave the same ports and click on “Apply” so that the keys are generated as in the image below:

When creating a new tunnel on the client side, new public and private keys are created.
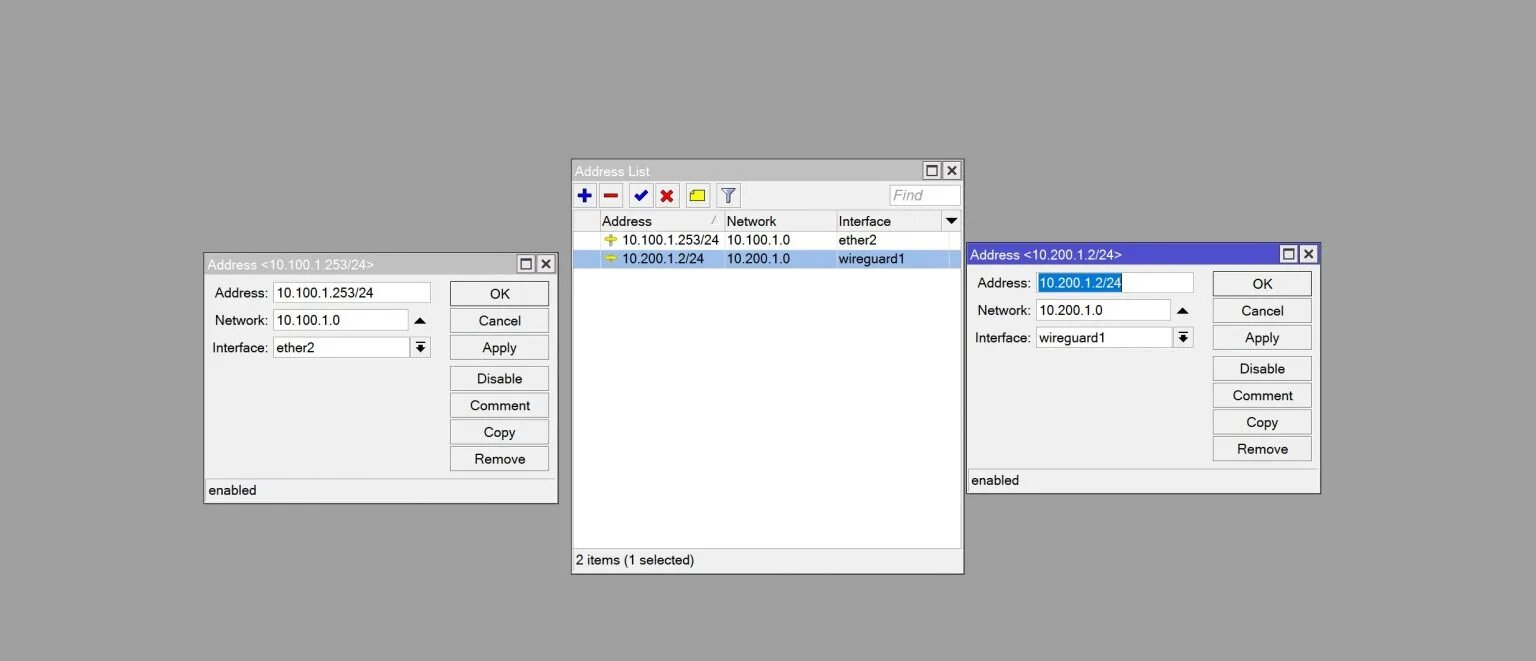
Creating networks on the client side.
As with the server, we will assign IP addresses to the client router.
Creating the Peers
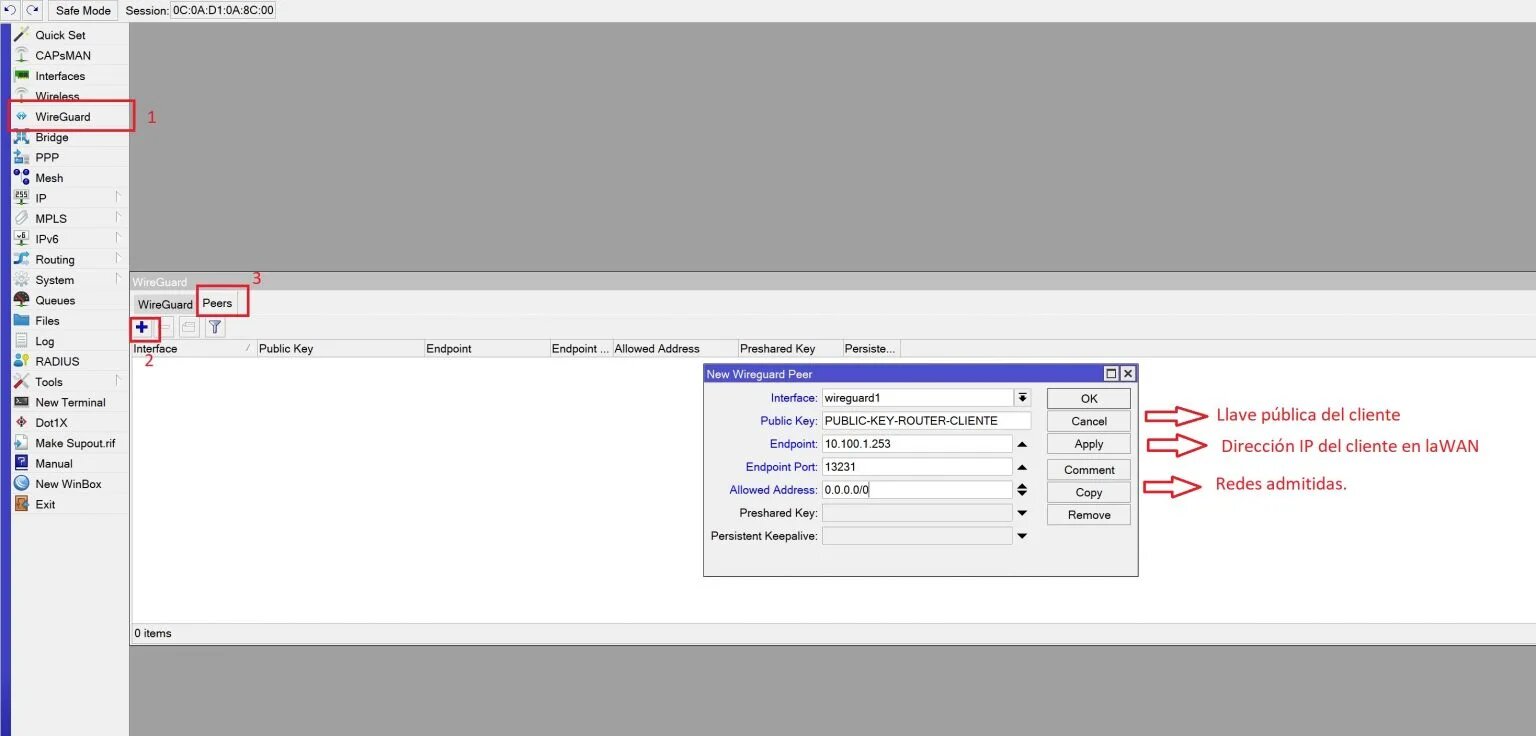
We have already created the tunnels on the server and the client, and we have also assigned IP addresses. All that remains is to create the peers so that communication can be established in the tunnel. We have the public keys of both the server and the client as soon as we create the tunnel, at which point the public and private keys are created.
For this peer configuration then, you will need to fill in the server public key on the client side and the client public key on the server side. We will see this in the following images.
Server Peers
Customer Peers
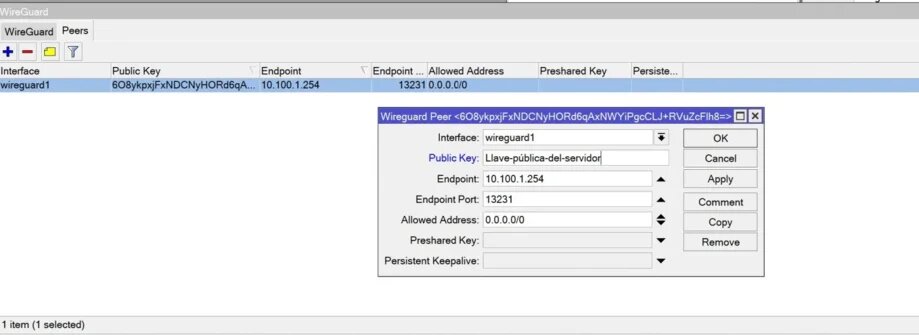
Here we must enter the server data and the public key.
Verification of operation.
We have already configured the tunnel with its networks and respective keys, we only need to see if it is really established. To do this, we will only need to ping the IP address of the remote tunnel, in the Wireguard interface.
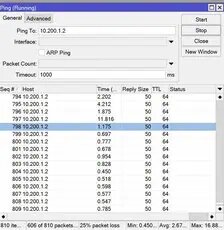
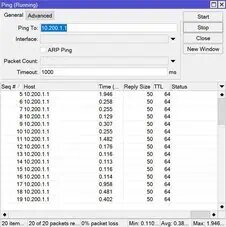
As we can see, we have a response, therefore, we confirm the tunnel is established and working, an additional test is to change some value in the key, the allowed networks or the endpoint and we would observe that we no longer have a response to the ping.
Is it possible to connect an end device to the WireGuard tunnel?
The answer is yes. We could connect a device such as a computer or a mobile phone to this tunnel, we just need the specific applications, depending on the operating system.
From the following link we can download them for all operating systems.
Download WireGuard client.
Is it necessary to make any additional changes to our Mikrotik router?
In case a mobile phone, tablet or computer is connected to our WireGuard tunnel with Mikrotik, we must take into account the supported networks. If we look at the previous configurations, there is a field that we fill in with the value 0.0.0.0/0, this field is "Allowedd Address" which is found in the peers section.
That field indicates the networks or IP addresses authenticated through our P2P tunnel. WireGuard works by encrypting data, based on networks and IP, that's what they call Cryptokey Routing Table.
In the client configuration, when the network interface wants to send a packet to its sole peer (the server), it will encrypt the packets for the sole peer with any destination IP address (since 0.0.0.0/0 indicates all networks). For example, if the network interface is asked to send a packet with any destination IP, it will encrypt it using the sole peer's public key and then send it to the endpoint.
In the client configuration, its only peer (the server) will be able to send packets to the network interface with any source IP (since 0.0.0.0/0 is all networks). For example, when a packet is received from a peer and is decrypted and also authenticated correctly, with any source IP, then it is allowed to enter the interface; otherwise, the packet is discarded.
So with this setup, when the server receives a packet with a source IP address, it should match its list of allowed addresses, so if we leave the network configured with the address 0.0.0.0/0 as the allowed address, as long as it has its public key, it will be able to join the network and the packet would not be dropped. Although it is recommended to configure the allowed networks, since we would have control over who can establish connections and who cannot.
Endnotes.
WireGuard is a faster and lower latency tunnel compared to OpenVPN and IPSEC, its configuration is much simpler than IPSEC, therefore an administrator would also benefit from this technology, it is only necessary to know the IP address, networks and interfaces and in this way we would know that the packet is secure, without complicated configurations in a firewall.