VLANs (Virtual LAN), also known as virtual local area networks, are a networking technology that allows us to create independent logical networks within the same physical network. The objective of using VLANs in a home or professional environment is to properly segment the network and use each subnet in a different way. In addition, by segmenting subnets using VLANs, traffic between the different VLANs can be allowed or denied thanks to a device. L3 such as a router or an L3 multilayer switch. At RedesZone we are going to explain in detail what VLANs are, what they are for and what types exist.
That the network works in the best possible way is something that every user or company seeks. This is something that affects many different factors, such as productivity or even at an economic level. Therefore, having a well-organized network is essential for optimal operation at all times.
What are VLANs?
VLANs or also known as "Virtual LAN" allow us to create logically independent networks within the same physical network, using manageable switches that support VLANs to properly segment the network. It is also very important that the routers we use support VLANs, otherwise we will not be able to manage all of them or allow or deny communication between them. Currently, most professional routers and even firewall/router-oriented operating systems such as pfSense or OPNsense support VLANs because it is a standard today. The use of VLANs provides us with the following:
-
Security. VLANs allow us to create logically independent networks, therefore, we can isolate them so that they only have an Internet connection, and deny traffic from one VLAN to another. By default, VLANs are not allowed to exchange traffic with another VLAN; it is absolutely necessary to ascend to the network level (L3) with a router or a multilayer switch, in order to activate inter-vlan routing, that is, routing between VLANs allow communication between them whenever we need it.
-
Segmentation. VLANs allow us to segment all computers into different subnets, we will assign each subnet a different VLAN. For example, we can create an internal management subnet for all routers, switches and access points, we can create a main subnet for administrators, another subnet for IoT devices and another different subnet for guests. That is, we can segment the main network into subnetworks with the objective that each subnetwork can use communications as they wish. Thanks to segmentation, we will be able to group a large number of devices within the same broadcast domain, even if they are physically very far away.
-
Flexibility. Thanks to VLANs we can place different computers on one subnet or another, easily and quickly, and have communication policies where we allow or deny traffic to other VLANs or to the Internet. For example, if we create a guest VLAN, we could prohibit them from using video streaming services.
-
Network optimization. By having smaller subnets, in environments where we have hundreds or thousands of connected devices, we will contain the broadcast in smaller domains, therefore, the network performance will be optimal, without having to transmit the broadcast messages to all the connected devices, which would cause the network's performance to drop radically and could even collapse. By using VLAN, we will have multiple broadcast domains on the same switch. In networks where traffic consists of a high percentage of broadcasts and multicasts, VLANs can reduce the need to send such traffic to unnecessary destinations. For example, in a broadcast domain consisting of 10 users, if the broadcast traffic is destined for only 5 of the users, placing these 5 users on a separate VLAN can reduce the traffic. Compared to switches, routers require more processing of incoming traffic, and as the volume of traffic passing through routers increases, latency on those routers also increases, resulting in reduced performance. Using VLANs reduces the number of routers needed because VLANs create broadcast domains using switches instead of routers.
-
Cost reduction. Due to the little need for network updates that are too costly, and thanks to a more efficient use of links and available bandwidth, it is possible to reduce costs when creating this type of networks. VLANs can be used to create broadcast domains that eliminate the need for expensive routers, further helping to reduce those costs.
-
Better efficiency of IT staff. They will make it easier for us to manage the network, because different users can share the same VLAN. When we implement a new switch, it will implement all the policies and procedures that the VLAN has pre-established. It will also make it easier to identify the function of a specific VLAN by providing it with a name.
-
Simple application and project management. These networks can aggregate devices and users to support certain geographic or business requirements. As they have different characteristics, the administration of a specific application, or hosting different projects, is much easier. Seventy percent of network costs are the result of additions, moves and changes of users on the network; every time a user moves on a LAN, recabling, addressing new stations and reconfiguring concentrators becomes necessary. and routers. Some of these tasks can be simplified with the use of VLANs, so if a user moves within a VLAN, reconfiguration of the routers is not necessary. Additionally, depending on the type of VLAN, other work may be reduced or eliminated, however, the full power of VLANs will only be truly felt when good management tools are created that allow network administrators to drag and drop users into different VLANs. or configure aliases, despite this savings, VLANs add a layer of administrative complexity, as virtual workgroups now need to be managed.
VLANs allow us to logically associate different users, based on labels, switch ports, their MAC address and even depending on the authentication they have performed in the system. VLANs can exist on a single manageable switch, to later assign each port access to a certain VLAN, but they can also exist on several switches that are interconnected between them, therefore, VLANs can be extended by different switches through the trunk links. This allows us to have the VLANs on different switches and assign a specific VLAN on any of these switches or on several simultaneously.
When we create and configure the VLANs on a router, they cannot communicate with each other. The only way the VLANs can communicate is by ascending to the network level (L3). We can do this in different ways:
-
Use a router/firewall with support for the VLAN standard. The switch will pass a trunk with all the VLANs and the router/firewall will register the different VLANs in its firmware or operating system, and will allow inter-vlan routing. It is possible that, by default, this routing is activated, but due to rules in the firewall, communication between VLANs is denied until we allow access.
-
Use an L3 managed switch. L3 manageable switches allow us to create IPv4 and IPv6 interfaces, so we can create an interface for each VLAN that we have configured on the switch and activate inter-vlan routing. This is a very good option to intercommunicate VLANs without the need for the router to take care of everything, generally these L3 switches are in the Core of the network.
To allow communication or non-communication of VLANs, ACLs (Access Control Lists) must be used, or the corresponding firewall must be configured to allow or deny traffic. For example, communication could be allowed from VLAN 2 to VLAN 3, but not the other way around, therefore, by correctly configuring the firewall and connection states, communication could be adjusted to the company's requirements.
Disadvantages of VLANs
We have just seen all the advantages and benefits of VLANs, but they also have their disadvantages and limitations, which must be taken into account when creating one. All this with the intention of taking better advantage of its functionalities and performance, saving installation and subsequent maintenance costs. Among them, some of the most important are:
-
Complex administration: If we have several VLANs, it can involve the same or even more work and cost than LAN networks. The truth is that this is one of the first points against it. And is not for less. Basically because you have to check that each device is correctly assigned to the corresponding VLAN without making a mistake.
-
Specific equipment and software: another disadvantage is that, in order to have a VLAN network, the truth is that you need to have the necessary network hardware, as well as the software that supports said connection. If there are no network switches that support VLAN, it will have to be purchased. So it is also an investment.
-
Isolation: If the network is very large, it is possible that several routers are necessary to be able to communicate without problem, which would increase the installation cost.
-
Congestion: This point only occurs if the VLANs are not configured correctly. Which implies that the speed with which data is transferred is also reduced.
-
Security: If a virus reaches the network, it can be distributed relatively easily throughout the network.
-
Latency: These types of networks are more efficient than WANs, but they are not as efficient as a LAN.
In addition to these points, we must also add that there is a greater risk of making some type of error during configuration. By simply configuring a VLAN incorrectly , the truth is that security or performance problems can be generated throughout the entire network. This is why you have to be careful during its configuration. Just as the management of different VLANs represents greater complexity and increases the probability of making errors.
Network segmentation
When creating different VLANs, it will be necessary to plan network segmentation. What is being divided into segments or subnetworks, which will function as small networks. This is largely used to increase monitoring, optimization and performance, while problems can be found more easily. Without forgetting the most important part, network security. Segmentation is very effective against unauthorized users, since access can be easily blocked. But to understand network segmentation perfectly, we must look at one term, the presumption of trust.
Before all this, network administrators were concerned only with keeping the network secure from the outside, leaving aside what may happen inside it. This occurred because it was assumed that all users within the network were trustworthy, and did not pose a threat, which is why few restrictions were generated. This is where the problems can begin, since the presumption of trust has been "taken to trial" on many occasions, since the personnel who are within the network can cause security breaches, leaks, among others. Which can leave the network practically clear for attackers, and they have access to important assets, even when these problems were detected.
This has led corporations to apply the Zero Trust strategy, which is basically a policy of not trusting anyone. At this point is where network segmentation appears, which generates new defenses against the possible problems that we indicated above. In many cases it can be done with virtual firewalls and VLAN networks, in which permissions can be generated for users or groups of users.
Network segmentation should not involve simply dividing a network into small or medium-sized networks, but should also meet the need to respond to the needs of the organization that depends on the network to operate. It has to do with the "main questions" in English, which we translate into Spanish as follows:
-
Where. It refers to the establishment of network segment points and the logic used to apply the segmentation of the organization's technological assets.
-
How. It has to do with the implementation of business goals with fairly refined access controls, simply with maintaining trust - in what and in who - continuous and adaptive to various circumstances.
-
What. Strengthen access controls by applying high-performance, advanced security measures across the network.
Of course, all of these essential questions will be answered based on the context of the networks that we manage and are working on. The way segmentation processes are applied can vary greatly. For example, micro-segmentation. Which can be applied according to the processes that are executed, applications used, existing endpoints and other criteria that can be considered.
What does it consist of?
It is a process that is responsible for dividing the network into small networks. Its purpose is to improve network performance and, above all, its security conditions. Segmentation works by controlling traffic in all parts of the network, you can choose to stop all traffic in one part that wants to reach another. Or, you can limit the flow that occurs on the network by the type of traffic, origin, destination and many other options. Any of these filters that you apply to the network are part of what are called "segmentation policies".
Some traditional segmentation technologies that can be cited are network equipment configurations for internal firewalls, Access Control Lists (ACLs) and the well-known VLANs (or Virtual Local Area Networks). The main disadvantage of these technologies is that at first it can be complicated to implement them, so the cost of doing so is high, but totally necessary today.
On the other hand, today we have software-defined technologies. They greatly simplify network segmentation by grouping and labeling all types of network traffic. These generated labels force the application of segmentation policies directly on the network equipment involved. The best thing about these technologies is that there is practically no complexity unlike traditional technologies.
As we mentioned previously, VLAN segmentation is one of the most popular ways to segment. How does it work? Creating a collection of isolated networks, each with its own broadcast domain within a data network. One of the things that network segmentation within a VLAN allows is to block access to it by cybercriminals who want to execute attacks of all kinds. In short, there are several security risks that can be mitigated. These are some:
-
Reduction of packet-sniffing, which is usually used to capture traffic at the Ethernet frame level, for the purpose of having sensitive user information.
-
Access to servers and services solely and exclusively to authorized personnel.
Segmentation is viewed as a set of ports, each of which can accept a variety of devices. These ports, which each represent a segment of the VLAN, have no functionality until a device has the appropriate permissions to access it, thanks to the segmentation processes. When a device wants to access one of these ports, identification is made using data such as MAC address, source IP, destination IP and much more.
Security in VLAN networks
As you can see, using VLAN networks is already a security measure as such. But once we have the network divided into these formats, we will have to implement security measures that adapt to these networks. This will help us maintain greater security for organizations' data and resources, while also preventing unauthorized access to information that may be highly sensitive.
Some of the security measures that we must take into account are:
-
Proper segmentation: Forming VLAN networks can be complex and simple at the same time. This is because it is necessary to properly plan all the VLAN networks that we are going to create. This will help us keep confidential information safe, and that the separation of networks is as appropriate as possible and adapted to the needs of the organization.
-
Port assignment: Establishing port assignment limits for VLANs helps us prevent unauthorized access. That is why only unauthorized devices and users should have access to the ports of the corresponding VLANs.
-
Strong passwords: Passwords are fundamental factors within any network. Therefore, they must be strong enough so that they cannot be easily broken, and at the same time protect the devices that manage the VLANs. They can be switches or routers. A change period is also recommended for them.
-
Authorizations: Strong authentication and authorization methods must be implemented. This will ensure that unauthorized devices and users cannot access VLANs that do not belong to them.
-
Encryption: Keeping information encrypted is essential in any network that needs high security. This will help us protect the information between the different VLANs, when the information has to go out to other networks.
What are VLANs for?
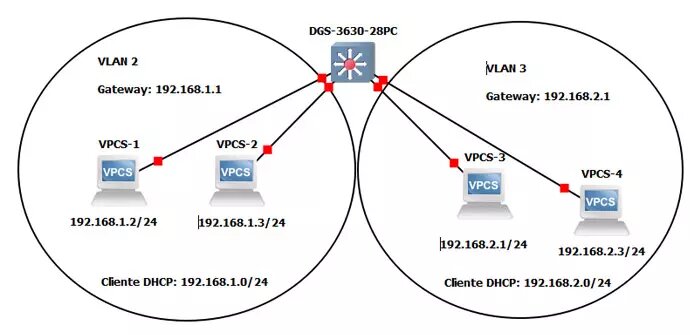
When we configure a local area network, whether in a home environment where we want to segment the different devices to connect, or in a professional environment, we use VLANs to have different subnets. Let's imagine that we are the network administrators of a school, we can create different VLANs for different uses and perform a much simpler administration of the network, in addition, we will be able to "contain" the broadcast messages in smaller broadcast domains, that is, , we will have small subnets to provide addressing to the dozens of computers we have, and not just one subnet where there are hundreds of connected devices. In this school scenario, we could perfectly have the following VLANs:
-
Management VLAN: we can create a management VLAN to access the router, firewall, all the switches distributed throughout the school and also the WiFi access points that we have, the monitoring systems will also be in this VLAN to continuously monitor the different network equipment.
-
School administration VLAN: all the PCs of the director, school secretary, teachers and other staff will be in this VLAN.
-
Student VLAN: all student equipment will be in this VLAN, whether wired equipment in the classrooms or via WiFi with a certain SSID associated with a VLAN.
-
Guest VLAN: the different smartphones and tablets of the students themselves, parents when they visit, etc. could be connected to this VLAN.
As you can see, a VLAN will allow us to segment the local network into several smaller subnets, specifically focused on a task in question. In addition, we will be able to provide security because the VLANs between them will not be able to communicate (or they will, depending on the configuration of the ACLs that we want). Thanks to VLANs, the overall performance of the network will improve, because we will be containing the broadcast in smaller broadcast domains.
Once we have seen what VLANs are and what they are for, let's see what types exist.
Types of VLANs
Currently there are several types of VLANs that we can use in different equipment, that is, in switches and WiFi access points. The different VLANs that exist are those based on the 802.1Q VLAN Tagging standard based on labels, port-based VLANs, MAC-based VLANs, and application-based VLANs, although the latter is not commonly used.
Native VLAN
The native VLAN, also called VLAN 1, plays a critical role in network segmentation. It is the default VLAN on a switch, and its primary function is to handle traffic that does not carry VLAN-tagged information.
When devices send traffic over the network without VLAN tags, this traffic is automatically routed to the native VLAN. This process is very important to ensure communication between devices that do not support VLAN tagging or in situations where tagging is not necessary. Therefore, the native VLAN is typically used in network environments to manage untagged traffic and facilitate communication between devices that are not configured to work within VLANs. Although VLAN 1 is designated as the native VLAN by default, it is important to note that in some environments, network administrators may decide to change the VLAN number associated with the native VLAN for security reasons.
From a configuration perspective, the native VLAN also plays an important role in switch trunking, where switches connect to each other to carry multiple VLANs over a single link. In these cases, traffic entering a trunk port without VLAN tags is automatically assigned to the native VLAN, facilitating a smoother transition of information between switches.
On the other hand, administrators must be aware of certain risks that VLAN 1 has. As it is the default VLAN, it can be vulnerable to security attacks if measures are not implemented to protect the system. Therefore, one of the most used processes to protect the native VLAN is to change its associated number.
802.1Q VLAN Tagging
It is the most used type of VLAN, it makes use of the 802.1Q standard to tag or untag VLANs. This standard consists of introducing an 802.1Q header within the Ethernet frame that we all know, with the aim of differentiating the different VLANs that we have configured. This standard does not encapsulate the original Ethernet frame, but rather adds 4 bytes to the original Ethernet header, in addition, the "EtherType" change is changed to the value 0x8100 to signal that the frame format has been changed.
When we are using the 802.1Q standard and we create the different VLANs on a switch, we can configure the different ports as “tagged” or “untagged”, that is, with or without tag.
-
VLAN tagged: the "tag" of the VLAN ID that we have configured is incorporated into the Ethernet frames. This type of VLANs are understood by all switches, by professional WiFi access points and by routers. One or more VLANs on a given port can be configured in tagged mode. In trunk links (from a router to a switch, from switch to switch and from switch to AP) they are usually always configured as "tagged" to "send" all the VLANs to them.
-
Untagged VLAN: in the Ethernet frames the tag that we have configured is removed. This type of VLANs are understood by all devices, but they are mainly used for end equipment such as computers, laptops, printers, IP cameras and other types of devices. . On a specific port we can only configure one VLAN as "untagged", we cannot set two VLANs as "untagged" because the final equipment would not "understand" anything.
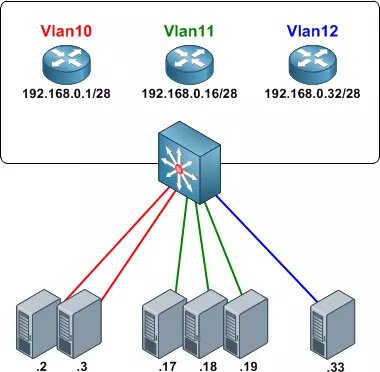
In the following image you can see that we have different VLANs created, and we will have an "untagged" column with the switch ports that are untagged. We also have a column with “tagged” where the tagged VLANs are. In this example, ports 1-4 and 9 are configured with professional APs and another switch, therefore, we will be passing tagged VLANs.

When we are using this standard, the switches also allow physical ports to be configured in different ways:
-
Access: these are the ports where we will connect PCs, printers, smartphones and end devices. This access port will have a VLAN configured as "untagged".
-
Trunk: carries one or more VLANs from one device to another, for example, if we want to connect a switch to another switch and "pass" all the VLANs or some of them, we will have to configure it in trunk mode, and select the VLANs that we want to pass as “tagged”.
-
Dynamic: depending on the type of packet the switch receives, it will be set as access or trunk. It is not recommended to configure the ports of a switch in dynamic mode for security reasons to avoid possible attacks.
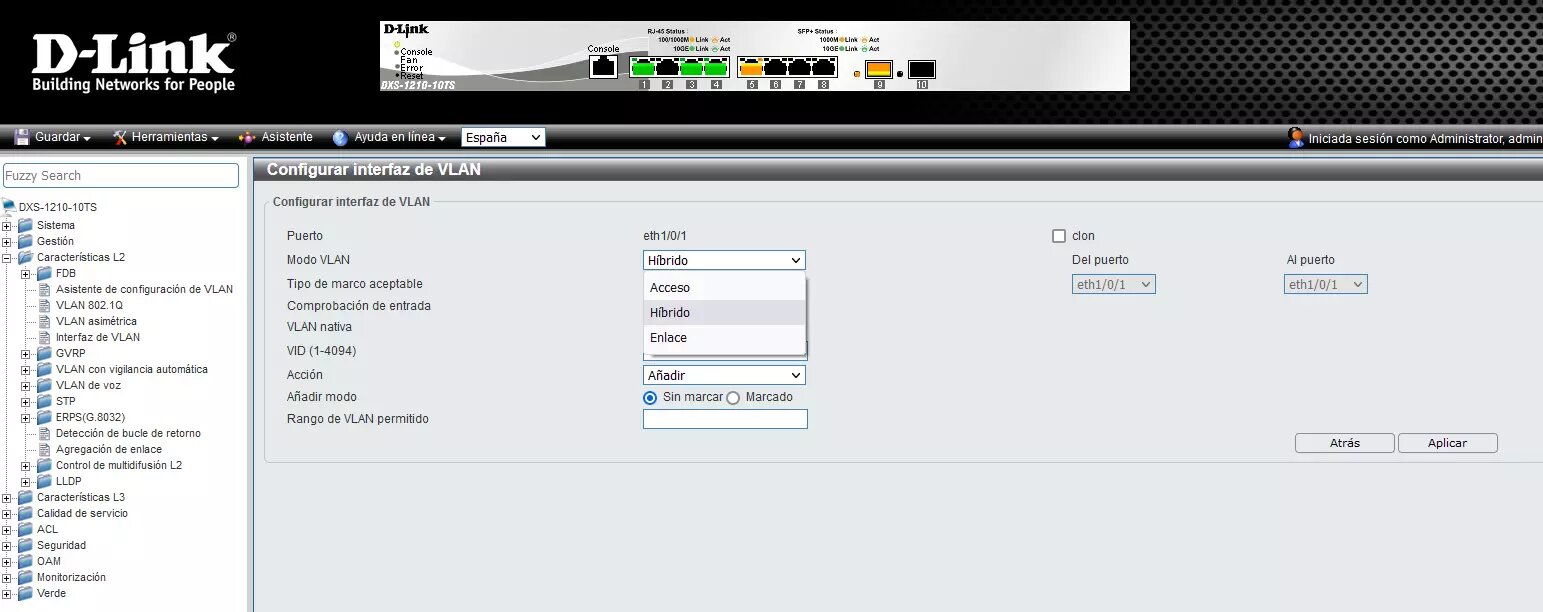
Depending on the port configuration that we are going to choose, we will have to fill in different parameters to correctly configure the VLAN. For example, if we select access mode (to pass the VLANs as untagged to the final device that we connect), it would be like this:

As you can see, when selecting access mode we must set the VLAN ID configured to remove the label and pass all the data to the final device. An important aspect is that advanced switches will allow us to configure the types of frames they accept as input; in this case, the normal thing for an access port is to only allow untagged frames.
Ports configured as "untagged" are synonymous with a port configured in access mode, and a port configured as "tagged" is synonymous with a port in trunk mode where we pass one or more VLANs.
Another very important feature of the 802.1Q standard is the Native VLANs, these native VLANs are a VLAN ID that is not tagged on the trunk links. If an untagged frame arrives on a port, it is considered to belong to the native VLAN. This allows interoperability with old devices, in addition, all traffic management for protocols such as VTP, CDP, Link Aggregation and others is managed through the native VLAN, which by default is the administration one.
Port-based VLANs
Also known as Port Switching in the configuration menus of routers and switches, it is the most widespread and used by very low-end switches. Each port is assigned to a VLAN and users connected to that port belong to the assigned VLAN. Users within the same VLAN have visibility to each other, although not to neighboring virtual local networks.
The only drawback is that it does not allow dynamism when locating users, and in the event that the user physically changes location, the VLAN would have to be reconfigured. In port-based VLANs, the decision and forwarding is based on the destination MAC address and associated port, it is the simplest and most common VLAN, for this reason low-end switches usually incorporate port-based VLANs and not based on the standard 802.1Q.
MAC-based VLANs
The reasoning is similar to the previous one, except that instead of being an assignment at the port level, it is at the device's MAC address level. The advantage is that it allows mobility without having to make changes to the switch or router configuration. The problem seems pretty clear: adding all the users can be tedious. Only the highest-end switches allow MAC-based VLANs, when the switch detects that a certain MAC address has been connected it will automatically place you in a specific VLAN, this is very useful in cases where we want mobility.
Let's imagine that we connect to our laptop on several Ethernet ports in our office, and we want it to always assign us the same VLAN. In this case, with MAC-based VLANs it is possible to do so without having to reconfigure the switch. In large business environments this functionality is very common to correctly segment teams.
Tagged VLANs
Here we will look at 802.1q labeling which is defined in the IEEE 802.1q standard. It allows a network device to add information to a frame at Layer 2, so that it can identify the VLAN membership of the frame. This tagging allows networked environments to have VLANs, which span multiple devices. A single device receives the packet, reads the tag, and recognizes the VLAN to which the frame belongs. On some devices, receiving tagged and untagged packets on the same network interface is not supported. If this happens, we must contact the administrators to solve the problem.
As for the interface, this can be a tagged or untagged member of a VLAN. Each of these network interfaces is an untagged member of VLAN only. In this case, this network interface is responsible for transmitting the native VLAN frames as untagged frames. But a network interface can be part of different VLANs, without the others being tagged.
When we configure tagging, we must ensure that it matches the configuration assigned to the VLAN on all its ends. And the port to which we connect must be in the same VLAN as the interface. We must also know that, if the VLAN configuration is not synchronized and propagated, the configuration has to be done on all units independently.
VXLAN
It is an extensible virtual local area network. This overlays Layer 2 networks on a Layer 3 infrastructure, encapsulating Layer 2 frames in UDP packets.
Each of these overlay networks is known as a VXLAN segment, and is identified by a unique 24-bit identifier. This is called VXLAN Network Identifier (VNI). As for devices, they can only communicate with each other if they are within the same VXLAN.
The advantages that this offers us are:
-
Greater scalability in virtualized cloud environments. This occurs because the VXLAN ID is 24 bits, which allows it to create up to a maximum of 16 million networks, which would be isolated. This exceeds what VLANs already provide, which have 12-bit IDs, and allow 4094 networks that are also isolated.
-
Greater flexibility when managing the entire connection.
-
Provides the option to use layer 3 functions in underlying networks.
-
The virtual network found at layer 2 is abstracted from the entire underlying network in physical format. This results in the virtual network not being visible to the physical network, which in turn provides some benefits such as eliminating the need for additional physical infrastructure, and reducing MC address duplication in VMs. that are on the same segment of the VSLAN.
Hybrid VLAN
As we have already seen, we have port-based and tagged VLANs. However, there is another alternative to these technologies. And they are Hybrid VLANs. They are based on the data packets being distributed according to the labeling assigned to them, and beyond this, the division of the network is marked by a deliberate connection of the ports.
All types of VLAN connections are valid, but choosing one or the other depends on the connections we want to obtain on the network. Or the level of security that we want to establish. Through these, work teams can be interconnected regardless of where they are located. And what is more important, without negatively affecting the security of the network or the internal segmentation to which it is subject.
Management VLAN
VLAN Management is a practice in network design that is used exclusively for the management of network devices. Its main function is to create an isolated environment where traffic related to device management, configuration and monitoring operations can flow without interference from user data traffic. This segmentation ensures that management activities are carried out in a controlled environment, contributing to network security and efficiency.
For better understanding, the Management VLAN establishes a private network within the main network, reserved exclusively for administrative tasks. Switches and other network devices can be configured to have an interface dedicated to this VLAN, thus allowing only authorized personnel to have system management access. This not only strengthens security by limiting access, but also makes it easier to detect and resolve problems, as well as apply firmware updates without affecting normal data traffic.
Control VLAN
On the other hand, the Control VLAN is implemented to transport traffic specifically intended for network control functions. This type of VLAN is designed to handle protocols essential to the operation and maintenance of the network, such as routing and tagging protocols. By separating this traffic from the rest of the network, the aim is to optimize overall performance and ensure more efficient management of internal processes.
The Control VLAN is essential to ensure that the low-level protocols that direct traffic on the network have a fast and reliable communication path. By isolating these protocols into their own VLAN, the possibility of interference with normal user traffic is reduced, giving a more tailored means of network operation and maintenance. This segmentation also makes it easier to implement changes to the network infrastructure without negatively affecting daily operations, contributing to the overall stability and efficiency of the network environment.
What is an isolated network and requirements to be secure
An isolated network could be defined as one that distributes packets to and from local systems. Also, even if it has defined routes to some other network, it does not carry messages to other networks. In that sense, your computers will not be able to communicate or network with other computers except those that constitute their own network. Thus, they would be isolated from other company networks in order to keep the information stored there more protected.
The best example of an isolated network that we could have in a company would be one completely separated from the main network. This means two things, one that we would not have access to it from the Internet because it would not have a connection of this type. The other would be that the company's other networks or subnets would not be able to reach it since they would not be connected to it via Ethernet cable, Wi-Fi, or other means.
Regarding the requirements that this isolated network should have to remain secure, our company should have a series of standards:
-
Network computers should have antivirus protection and be manually updated at least once a week.
-
We must have a device control system for each machine, which prevents the connection of USB drives or other storage devices, except those that are on a list of trusted devices.
-
Prohibition of the use of smartphones and other devices with an Internet connection in the place where our isolated network is located.
At first glance, it might seem like an almost perfect situation, very difficult to breach, but sometimes mistakes are made that end up harming your security.
The danger of smartphones that offer Internet connections
In many cases, security experts believe that an isolated network does not need special protection to protect its information. The reason they give is that threats cannot penetrate the network. However, they are wrong because isolation is not a sufficient guarantee to stay safe.
One of these typical failures occurs due to human error and overconfidence. Employees in charge of updating antivirus or other programs find this weekly task of updating them boring and tedious. Then they are tempted to use a smartphone, a USB modem or other means to be able to use a computer with an Internet connection and perform an automatic update.
Simply doing so does not involve network attacks, Internet malware, or other security problems. The problem usually comes because those in charge of updating the antivirus do not do it weekly. Cybercriminals can then infect that computer with Trojans, spyware, and end up gaining access to the entire isolated network. Thus, from that moment on they will be able to collect all the information they want until an antivirus update cuts off their access or they are detected.
Practical examples of using VLANs in WiFi
VLANs are widely used in the world of WiFi with professional WiFi access points, either in standalone mode (individual management of access points) or through WiFi controllers (whether local hardware controllers, WiFi controllers through software installed on a server or in a virtual machine or WiFi drivers in the Cloud of the WiFi access point manufacturer.
The objective of VLANs in a professional WiFi access point is to configure a VLAN for each SSID that we configure. Currently, most professional APs allow us to create up to 8 SSIDs for each frequency band, and there are even some higher-end models that allow us to create up to 16 SSIDs for each frequency band. If we associate a VLAN with each of these SSIDs, we can not only segment the network through the wired network, but also our own wireless network.
The configuration of the APs is quite simple, we simply have to configure a trunk link to the access point in question, to later configure an SSID for each of the VLANs that we have configured. For example, with Nuclias Connect, which is the centralized management platform for WiFi access points from the manufacturer D-Link, we can configure the APs to receive all VLANs via LAN, and subsequently assign each VLAN to a certain SSID that we create.
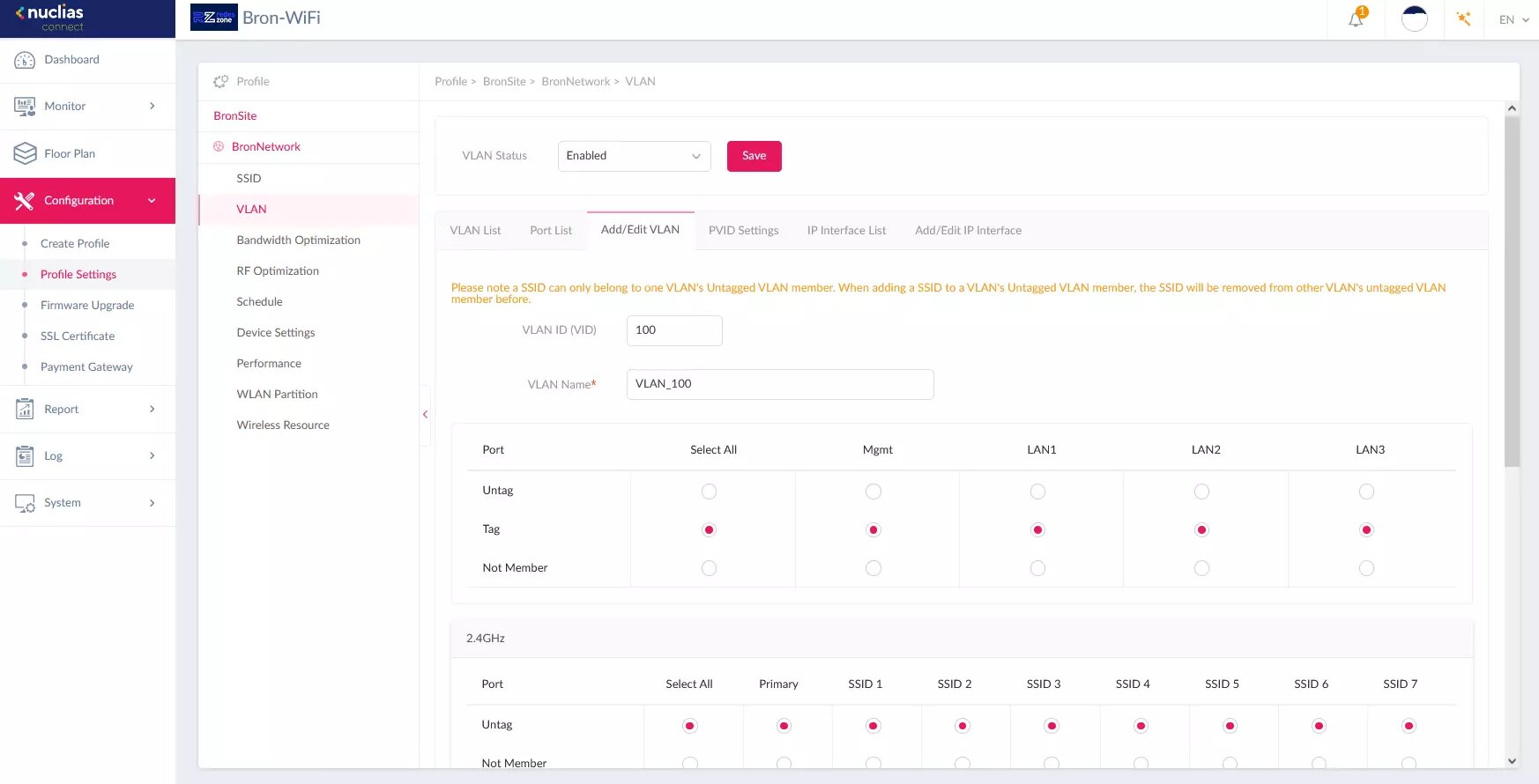
Thanks to this, we will not only be able to segment the wired network, but also the WiFi wireless networks based on the SSIDs associated with the different VLANs that we have. In the case of Nuclias Connect, we will only be able to create a total of 8 SSIDs, the primary SSID that we will always have, and a total of another 7 additional SSIDs for each WiFi frequency band. As you can see, we also have the possibility of configuring the "Management" port with an untagged or tagged VLAN, depending on whether we have a management-only VLAN in our local network, in this way, all the equipment that is responsible for Network management such as WiFi controller, APs, switches, routers and other devices will only be accessible through this management network to adequately protect all access.
A good security practice would be to create a VLAN with a specific SSID for "Smart Home" devices, such as cable or WiFi TV, IP cameras and other types of devices such as smart plugs, WiFi relays and other series of devices classified as "Smart Home". Next, we can configure a specific SSID for the main network, where we connect the smartphone and the main laptops or ultrabooks, with the aim of having the maximum possible privileges. Finally, we can create an SSID for guests that is quite limited in terms of access to other services on the local network and even limit this specific SSID to prevent it from exceeding a certain download and upload speed, limit access to web content and everything else. that we want.
Dedicated VLAN
In many companies, there is always some task available which is fundamental or critical within the production line organization chart. These tasks are characterized at the computer level by requiring very specific conditions, and in different aspects. In these cases, a VLAN that acts independently can be a great idea so that this task can be carried out in the most appropriate way possible. In these cases, said activity may require very specific requirements.
-
Security: With a dedicated VLAN, the appropriate privacy policies can be applied for the task at hand. But in this case, we will have a much greater degree of customization, which can greatly reduce the probability of attack. And in case it occurs, have that defense capacity that does not allow it to spread through other networks.
-
Performance: In critical tasks, performance can be essential, which is why a VLAN is more than recommended. This will allow us to allocate all the bandwidth that is necessary, allowing the task to operate more efficiently and with more capacity. This will avoid network congestion problems.
-
Manage traffic: Managing traffic individually is much easier than if it is a general network. In these cases, QoS policies can be implemented to help ensure that the task has the necessary priority to be able to develop normally.
-
Isolation: Maintaining privacy and confidentiality in many cases is of vital importance. Therefore, having critical tasks isolated can be of great help to maintain all these requirements in a simpler and more personalized way.
-
Flexibility: The VLAN provides much more flexibility when it comes to configuring the network in a specific way. This means that something completely different can be done depending on the needs of the activity in question.
When to use a VLAN?
Since the main benefits of this type of network are to improve performance and apply stronger security measures, it is relatively easy to know when we need a VLAN to apply any of these measures. Some examples may be safeguarding personal information of a staff, such as the different departments of a company, so that they are not visible to each other.
We can also use it when we need to simplify management when managing different group policies, in this way, they can be applied differently to all the devices that make up the same VLAN. In the same way, restrictions can be applied regarding certain accesses that computers or users that belong to the same VLAN can have.
In terms of security, they are very useful when it comes to isolating failures, and what that entails, the speed at which they are resolved. Therefore, it may be advisable if very sensitive data is handled, such as in the health or financial sector.
But something that we cannot forget when establishing this type of networks is the material used. All hardware must be of good quality, and for this it is best to look for the most reliable brands on the market. If we purchase low-quality components, for the simple fact that they are cheap, it can be very expensive. And we're not just talking about the need to spend more money on new equipment, but also on performance. These types of very cheap components can have many shortcomings in terms of performance. Therefore, it will negatively affect how the network works. Another issue is quality standards. This is very important to know that the device will give us the performance for which we bought it.
On the other hand, there is security. Buying bad products can be dangerous. Among other things, routers can get hot at times. Or without going any further, the network cards themselves that we install in the computers. Everything must be of good quality, so that the performance is correct and they do not degrade very quickly. And also that they are safe.
How to know which one I need
The first thing we must consider is the topology of our network. How all the devices and servers that make up our network are connected is a very important step in order to know which VLAN we are going to need. If we have a flat topology, where all devices are connected to a single switch, the best thing would be a VLAN to separate traffic and thus increase security. On the other hand, if we have a more hierarchical topology with several switches connected at different levels, it is likely that not as many VLANs will be necessary, or directly necessary.
On the other hand, we must take into account the size of the network and its complexity. If we have a smallish network with few devices, it is likely that a VLAN is unnecessary. On the other hand, if our network is very large and complex, with many connected devices and subnets, it may be highly advisable to create several VLAN networks so that the traffic is separated and the security of the system is increased.
Traffic also plays a fundamental role in the organization chart. Knowing what type of traffic passes through our network will help us decide. If this is voice and video, we may need a VLAN that is capable of separating and ensuring the quality of both services. In the same way that if we have very sensitive data, such as banking or clinical data, it is best to have separate VLAN networks so that security is greater.
And finally, we will have to look at the security policies of our company or organization. If it has very strict security policies, which in themselves require physical and logical separation of traffic, then we need one or more VLANs. Which will help us comply with all these policies, and even improve the internal security standard we have.
Nowadays, segmenting a large network is essential, both with the aim of providing greater security to the entire network, and to have different devices with different uses. As you have seen, VLANs are a technology that will allow us to correctly segment wired and wireless networks, ideal for having the best possible security, control of all connected equipment, and network optimization to avoid broadcast storms.
So you can have an isolated network in domestic environments
Sometimes you too may want to create an isolated local network in your home environment. Nowadays, remote working from home is increasingly on the rise. However, not all family members are very strict when it comes to safety. In that sense, some type of malware could be spread that affects the local network. That is why using a second router that we have at home we could create two networks:
-
The 192.168.1.X range for working devices.
-
The 192.168.2.X range for entertainment devices and for the rest of the family.
Also some manufacturers such as ASUS and the AVM FRITZ!Box offer technology to isolate WiFi clients, so that they cannot communicate with each other with other wireless clients. The same could be done using wired networks. Let's give an example with a FRITZ!Box so that the wireless clients do not see each other:
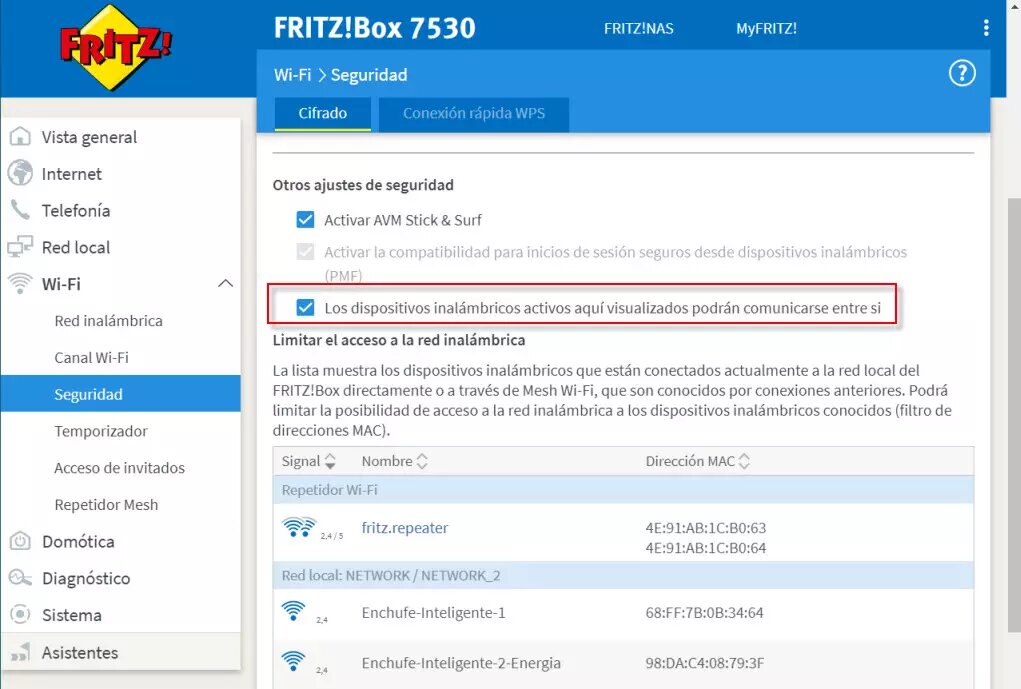
In this case, if we deactivate the red box, the devices will not be able to communicate with each other. However, we could also create a guest network from scratch that is completely isolated from the main network, in this way, we can configure a wired and wireless guest network, where they cannot communicate with the main wired or wireless network. In addition, it would also be advisable to segment the local network into different VLANs, but to do this you will need a router compatible with VLANs and also a manageable switch to create them correctly.
As you have seen, having an isolated network is not totally secure, since human intervention or poor configuration could make it vulnerable and be attacked. Additionally, in home environments we could also configure an isolated guest network, so that they do not communicate with the main network.





